By: Brandon Wick, Sr. Integrated Marketing Manager at the Linux Foundation
Cybersecurity has been in headlines a lot lately and with good reason. In 2020, the average time to identify a breach was a whopping 207 days producing an average data breach cost of $3.86 million (IBM). Already on the rise over the past decade, COVID-19 has accelerated this trend with Cybercrime up 600% due to the pandemic (PurpleSec). On May 12th of this year, the White House announced a sweeping Executive Order on Improving the Nation’s Cybersecurity to guide collaborative efforts in the public and private sectors to counter increasingly sophisticated, evolving, and damaging cyber attacks.
Because open source software is so prolific in our economies and modern technology infrastructure, it obviously has a major role to play in confronting the cybersecurity challenge and bending the arc of the struggle towards collective safety. Given that 90% of a modern application’s code base is open source (Sonatype), it’s critical to develop open source guideposts around security best practices and launch initiatives aimed squarely at the threat. Recognizing this, Google announced $10B to advance cybersecurity efforts — including $100 million to support third-party foundations, like the Linux Foundation’s Open Source Security Foundation (OpenSSF) that manage open source security priorities and help fix vulnerabilities.
The Linux Foundation recently published a detailed blog that details how we are aligned with the President’s Executive Order and are working to help improve the security of open source software. I encourage you to read this post to get an understanding of how the Linux Foundation approaches critical security elements, including Best Practices, Encryption and Data Confidentiality, Supply Chain Integrity, Software Bill of Materials (SBOMs), Vulnerability Disclosure, Critical Software, Internet of Things (IoT)), Security Labeling, and more. I will also note the Linux Foundation has recently launched a new training course Generating a Software Bill of Materials (LFC192) with Software Bill of Materials (SBOM) elements and open source tooling available for those interested in expanding their security skillset.
Specific to the open source networking ecosystem, LF Networking (LFN) sets the security direction at the Board, Technical Advisory Council, and new LFN Security Forum levels, while simultaneously empowering LFN projects to enact security practices specific to their communities. LF Networking views open source security as a continuous improvement process — one that tracks with a project’s maturity level and phase of adoption. Throughout the project lifecycle, investments are made in security process definition, security audits, and security threat modeling. In addition, license scans are run against several LFN project code bases monthly with results and SBOMs published in public repos.
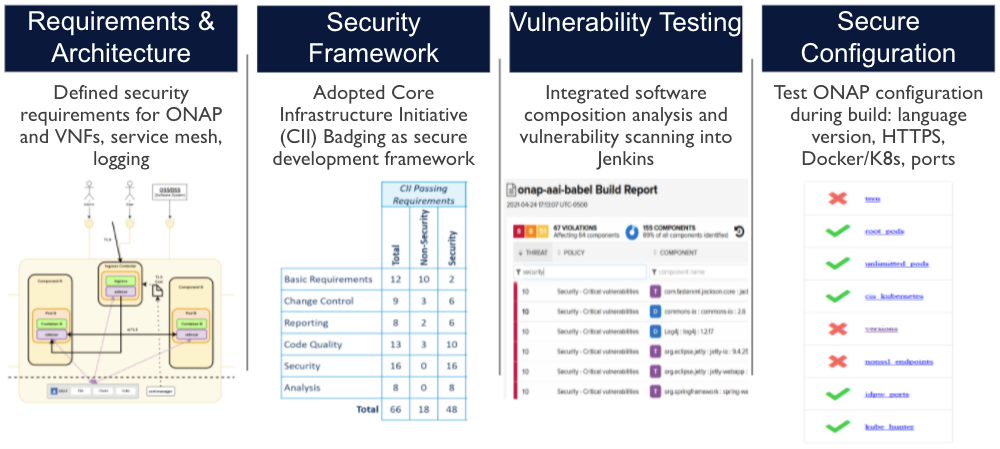
As a mature project with an active security subcommittee, ONAP is a good example of open source project security innovation that includes the following elements:
Other LFN Projects are innovating in security and here are few highlights:
- Anuket: Enacts multiple aspects of security working in conjunction with cloud infrastructure to support networking workloads
- FD.io: FD.io’s Vector Packet Processing (VPP) exposes a number of security features usable by developers.
- ODIM: Uses SSL based encryption for all APIs, token based authentication, storing encrypted credentials, and monitoring new Common Vulnerabilities and Exposures
- OpenDaylight: Enables users to automate their networks and provides network-wide visibility to gather, filter, and analyze real-time and historical telemetry data
- Tungsten Fabric: Contains security auditing of both system components and upstream packages with audits as part of testing and deployments, with hardening added to every release
- XGVela: Conducts seed code scans and is evaluating the security standards and making them a part of its future releases
While cybersecurity threats facing the global networks we rely on are significant, open source is inherently well equipped to adapt to the evolving security landscape. By motivating leading edge development with vulnerability detection and code design best practices built in, developers can create quality, secure software for commercial software. As Linus Torvalds famously said: “given enough eyeballs, all bugs are shallow”.
We welcome you to learn more about networking software security at the Open Networking & Edge Summit, Oct 11-12. Here is a subset of sessions that highlight innovation in LF Networking and . adjacent open source communities. We hope to see you there!
- Keynote Panel: Security across Cloud, Telecom and Edge – in an Open World – Priyanka Sharma, Cloud Native Computing Foundation; Amy Zwarico, AT&T; Malini Bhandaru, Intel; Will Townsend, Moor Insights & Strategy: https://sched.co/lSzM
- Open, Programmable, Secure Network & Edge – US GOV OPS Mini Summit: https://sched.co/manq
- 5G – Prioritizing Security Now – Brian C. Newman, Verizon: https://sched.co/lSul
- Low Trust Edge Network? No Problem – Get Great Performance and Security Using Calico, VPP, and WireGuard – Chris Tomkins, Tigera & Nathan Skrzypczak, Cisco Systems: https://sched.co/lStS
- Lightweight EVE-OS Carries Heavyweight Security to Safely Enable Edge Software Orchestration – Kathy Giori, ZEDEDA Inc: https://sched.co/lSuo